AP Syllabus focus:
‘Debates about collecting digital metadata involve whether surveillance policies protect public safety or interfere with individual rights.’
Digital surveillance raises core Fourth Amendment questions in a modern form: what counts as a “search,” when warrants are required, and how to weigh security goals against privacy in the age of data trails.
The Fourth Amendment Framework Applied to Data
The Fourth Amendment limits government power by prohibiting unreasonable searches and seizures and typically requiring probable cause and a warrant.
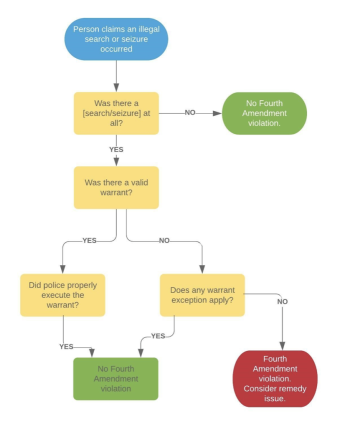
Flowchart showing the basic Fourth Amendment analysis: (1) did a search/seizure occur, (2) was there a valid warrant, and (3) if not, does a warrant exception apply. This kind of decision-tree mirrors how courts and lawyers structure arguments about whether collecting digital metadata is “reasonable” and what remedy follows from a violation. Source
In digital contexts, the key issue is whether obtaining data is a “search” that intrudes on privacy interests.
What “Digital Metadata” Means for Fourth Amendment Analysis
Digital metadata: Data about communications (such as numbers dialled, time, duration, routing, device identifiers, or location pings) rather than the message content itself.
Because metadata can be aggregated at scale, it may reveal intimate patterns (contacts, routines, associations), even if it is not “content.”
Surveillance Policy Tension: Public Safety vs. Individual Rights
The syllabus focus is an ongoing debate: collecting digital metadata may help identify threats, map networks, and detect criminal activity, but it may also chill speech and association and expose large amounts of personal information unrelated to wrongdoing.
Public safety rationales
Speed and prevention: rapid identification of suspects or networks after an attack.
Pattern analysis: using metadata to detect unusual behaviour or connections.
Resource efficiency: automated filtering can prioritise leads when threats are time-sensitive.
Civil liberties concerns
Breadth and spillover: bulk collection can capture data from millions of innocent people.
Chilling effects: people may avoid lawful speech or associations if they expect monitoring.
Data misuse risk: mission creep, unauthorised queries, or insecure storage can magnify harms.
How the Supreme Court Has Approached Metadata-Related Privacy
Fourth Amendment doctrine in this area often turns on whether individuals have a reasonable expectation of privacy in the data and whether the government’s method resembles targeted investigation or broad monitoring.
Reasonable expectation of privacy and the “third-party” problem
Third-party doctrine: The principle that information voluntarily shared with a third party (like a phone company) may receive reduced Fourth Amendment protection.
This doctrine historically made some metadata easier for government to obtain, because service providers already held it for business purposes.
Key developments that shape today’s debate
Katz v. United States (1967): shifted focus from physical trespass to privacy expectations, supporting the idea that some communications-related monitoring can be a search.
Smith v. Maryland (1979): upheld use of a pen register for dialled numbers, reinforcing third-party doctrine logic for certain phone metadata.
United States v. Jones (2012): GPS tracking triggered Fourth Amendment concerns; several justices emphasised how long-term tracking can reveal a detailed portrait of life.
Carpenter v. United States (2018): held that accessing historical cell-site location information generally requires a warrant, signalling that some modern metadata is so revealing that older third-party assumptions may not control.
What the Debate Looks Like in Practice
Policy disputes often centre on whether surveillance is targeted (narrowly focused on specific suspects) or bulk (collecting first, sorting later).
Common points of dispute
Scope: collection limited to identified targets vs. broad collection of many people’s records.
Authorisation: traditional warrants vs. specialised national-security procedures.
Oversight: internal auditing, court supervision, congressional reporting, and transparency.
Minimisation: rules limiting retention, queries, and dissemination of nonrelevant data.
Why This Matters for AP Government
This subsubtopic connects constitutional principles to modern governance: how institutions define “reasonable,” how courts adapt older doctrines to new technologies, and how democratic accountability works when surveillance is secret or technically complex.
FAQ
Metadata is often regulated under different legal authorities and standards than content, partly because it has been viewed as less intrusive.
However, modern analytics can make metadata highly revealing, prompting newer limits in some contexts.
Minimisation refers to safeguards that restrict how collected data is handled, such as:
limiting retention time
restricting who can query datasets
masking identities unless necessary
It matters because it aims to reduce privacy harms when non-target data is incidentally collected.
Many metadata records are generated and stored by service providers for billing, routing, or security.
This raises issues about compelled disclosure, transparency reporting, and how much constitutional protection applies when data is held by intermediaries.
Encryption can protect content but may still leave metadata exposed (e.g., routing, timing, endpoints).
Newer protocols can reduce available metadata, shifting surveillance toward device-level data, location signals, or provider-held logs.
Oversight may include judicial review in specialised courts, internal compliance offices, inspectors general, and congressional intelligence committees.
Debates persist about whether these checks are sufficiently adversarial, transparent, and effective given secrecy and technical complexity.
Practice Questions
(2 marks) Explain one reason why bulk collection of digital metadata raises Fourth Amendment concerns.
1 mark: Identifies a valid concern (e.g., mass collection affects many innocent people; chilling effect; reveals detailed life patterns).
1 mark: Links the concern to the Fourth Amendment (e.g., “unreasonable search,” expectation of privacy, warrant/probable cause).
(6 marks) Using Supreme Court reasoning about privacy in the digital age, evaluate the argument that collecting digital metadata can be constitutional while still protecting public safety. In your answer, refer to one relevant case and discuss one counterargument.
1–2 marks: Explains how digital metadata collection can serve public safety (e.g., network mapping, faster threat detection).
1–2 marks: Uses one case accurately (e.g., Carpenter: certain metadata like historical location generally needs a warrant; Jones/Katz/Smith as relevant).
1–2 marks: Develops a counterargument grounded in constitutional reasoning (e.g., bulk collection is overbroad; third-party doctrine may be outdated; chilling effects; inadequate oversight), with evaluation rather than assertion.

